Criminals are in the business of making money. As more of our lives move to the Internet, criminals move there as well because money can be made. In fact, the Internet gives criminals a higher degree of anonymity to carry out their attacks. Targets can be robbed from across the globe minimizing risk. Ransomware is an example of a low-risk crime with a high level of reward for the attackers. And a perfect example of this is HIPAA ransomware attacks. Physicians, especially those in smaller practices, are easy targets for attackers to make some quick money.
What is ransomware and why is it so profitable for criminals?
Ransomware is malicious software that invades a computer and begins to encrypt all of the data it finds on the computer. It is careful to leave the operating system alone as it targets your documents, pictures, and data for programs like QuickBooks. Some ransomware is able to move across your network and perform the same attack on each computer on the network.
Once your data is encrypted, the ransomware will show you a warning telling you that all of your data has been encrypted and offering to give you the password to decrypt it all for a fee.
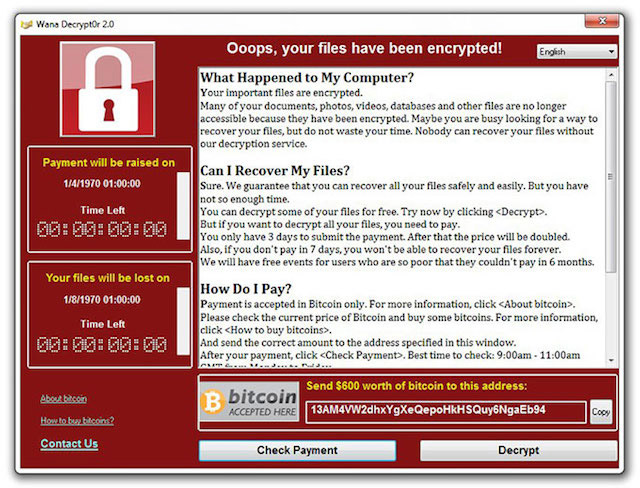
In other words, your data is being held ransom until you pay up.
Payment is handled via Bitcoin, the semi-anonymous online money that can be sent anywhere in the world. This helps attackers to work from the safety of other countries with little threat that they will be caught or punished.
For the criminal, the end result is low risk but high reward. How high is the reward?
Jackson County pays $400,000 ransom to attackers
In March of 2019, the computer network for all of Jackson County, Georgia became infected with a ransomware strain known as Ryuk. This was created by a shadowy cybercriminal gang operating out of Eastern Europe. This group is focused on healthcare and local governments because they know that these are usually easier targets that will pay the ransoms.
In the case of Jackson County, most of the county’s IT systems were affected. The FBI was notified and a cybersecurity firm was called in. The firm negotiated with the attackers for a payment of $400,000. After the payment was made, the county received the decryption key and began to decrypt their network.
The end result for the criminals? Low risk as they are unlikely to be found or extradited, with a high reward of $400,000.
Why is HIPAA ransomware attacks worse than attacks for other businesses?
Most businesses in the United States aren’t under compliance regulations such as HIPAA. HIPAA requires Covered Entities and Business Associates to actively protect the data in their control. There strict penalties for those who do not comply and are breached. this means that sites that become infected are faced with not only the ransom itself but also the potential for federal fines and also lawsuits by patients. HIPAA ransomware attacks have the potential to be far worse and the overall cost to physicians is much higher.
Because of this, attackers target the healthcare industry. They know that sites must be back up and running as quickly as possible and also have HIPAA regulations to contend with. This increases the chances of the ransom being paid. Many of those infected may also want to keep it quiet so that they can avoid reporting the breach. However, this usually doesn’t work out well.
Those that choose to not pay the ransom often have enormous expenses to pay for the cleanup. The city of Atlanta chose not to pay a ransom of $51,000 and instead have run up a bill of over $17 million.
What can your practice do to protect against HIPAA ransomware attacks?
The best defense against ransomware is to have good backups. If your data is backed up in a secure way, then there is no reason to pay the ransom. Just restore from the backup and you are back up and running.
However, if your only backup is a hard drive that is connected to your server, then by the time you notice the ransomware infection, the drive will already be encrypted. Ensure you have a copy of data offsite and not connected to your network in any way.
The second step you should take is to have commercial grade anti-malware software installed on each computer on your network. In the past, this software was called anti-virus but as the types of threats have evolved, so has the protection. Do not use the free versions of these programs. After the trial period has expired, they will no longer offer real-time protection. This means you will have no protection against a ransomware attack.
The next step is to keep your computers and all software up to date. Many types of ransomware make use of security holes to infect your computers. Keeping them up to date closes these holes and protects your devices.
The final step is training. Your staff needs to be trained on what to look for and how they can help prevent these types of attacks. Most attacks rely on some form of user help to be successful. Training will give your staff the tools they need to notice suspicious activity that leads to infections.
Ransomware can be a low-risk high reward system for cybercriminals. Add to those industries like healthcare that have additional regulations on them like HIPAA, creates a situation where criminals have a higher chance of getting paid. This is why healthcare is often one of the targets of these criminal gangs. HIPAA ransomware attacks can be very costly to Covered Entities and Business Associates because of the risk fines and patient lawsuits.
Take steps now to protect your data and your practice so that you don’t end up like Jackson County.
[DISPLAY_ULTIMATE_SOCIAL_ICONS]