Most people are familiar with the many types of devices in a home or business that can be connected to the Internet. This has given rise to a new class of devices known as the Internet of Things, or IoT. There is no shortage of the types of devices that are able to do this, ranging from home automation systems, appliances, toothbrushes, all the way to clothing. But for many of these devices, IoT security is an afterthought, if it’s even thought about at all. While the danger to end users is real, the risk for medical practices is considerable. In this article, we are going to discuss the dangers that IoT devices can pose to both the average technology user and to medical practices. As we will see, in some cases, having these devices connected is a spectacularly bad idea.
OK, so what actually is the Internet of Things?
The Internet of Things (IoT) consists of a wide range of devices that use several different methods of connection. However, for the purposes of this article, we are going to focus on those that use WiFi or Ethernet.
These devices can be the everyday things such as a smart thermostat so that you can remotely change the temperature in your house. In fact, the multitude of devices that comprise a smart home are all included in IoT. Here are some examples you probably have in your own home:
- smart light switches
- smart power plugs
- smart outside lighting
- doorbell cameras
- nanny cams
The IoT has also extended into healthcare by enabling providers to extend their reach outside their physical practices. IoT devices have created home monitoring systems that allow physicians the ability to keep track of a patient’s health when not in the clinic by sending data to the physician over the Internet. This also helps the patient by reducing the number of necessary office visits and keeping costs down.
IoT in Healthcare
Within healthcare, the goal is always to improve outcomes and reduce costs to deliver healthcare services. Using IoT devices known under the umbrella of remote patient monitoring (RPM), physicians can get the steady stream of data to, more accurately and cost effectively, treat patients. Data can include patient vitals, sleep apnea related measurements, and blood glucose levels.
All of these devices use Wi-Fi to connect to a local network in your home or practice and, then, to the internet. By doing this, the devices can either be accessed remotely, for example with smart home devices and nanny cams, or they can stream data from a home to another location such as s physician office. The IoT has greatly increased convenience and the ease to which we can have constant access to various types of data. Being able to monitor your baby or your home while you’re away traveling, all while doing this on your phone, was unthinkable not very long ago. We are now provided with very useful capabilities which are only increasing in power and flexibility as the technology matures.
IoT Security, Or Lack there of
All of this increased capability also comes with additional security concerns. This is especially the case when handling patient data. The unfortunate truth is that many vendors create products with little or no thought given to security. Because of this, IoT devices, which are often fully functional computers themselves, are connected to internal networks and are completely vulnerable to attack. One of the dangers is because of hard-coded admin credentials. These are an admin username and password that are written into the core operating system of the device and cannot be changed. The credentials often leak onto the web and then are integrated into automated attacks by cybercriminals, hackers, and nation-state cyberwarriors.
Another very concerning issue is that many vendors will not patch vulnerabilities in their devices when they are found. Security researchers may stumble upon a vulnerability in a specific device. They will responsibly disclose this to the vendor so that it can be addressed, only to have the vendor ignore it entirely. It is often deemed too expensive to patch, especially for devices nearing or already at end-of-life. This means that there are millions of unpatched devices live on the Internet, just waiting for an attacker to locate them.
Vendor Insecurity
Here is an example of each of these issues.
Cisco has been hit with two separate issues concerning hard-coded passwords. This led to attackers being able to gain access to the root account using these credentials that had been released online.
In 2019, a series of vulnerabilities was discovered. Vendors were updated to that they could release patches. However, some vendors did not and others did not release patches for end-of-life devices, leaving millions of devices unpatched on the Internet. While vendors aren’t at fault for not patching devices they no longer support, the fact remains that corporations and end users are still using many of these devices. They may not realize that the device has reached end of life and have forgotten about the device entirely. That is the nature of IoT, we plug it in and then forget about the device itself. When was the last time you updated your security camera firmware at home of that of your router?
Another security issue is the lack of proper configuration of devices once installed. This may mean putting it on the network in a place where it is accessible from the Internet and/or leaving the default admin credentials in place. If you think that no one would ever plug something like a baby cam or their home’s security cameras up in a way that the whole world can see it, well, then strap in, because I have something to show you.
Hacker Search Engine?
Shodan is a search engine for anything connected to the Internet. It became famous because it allows anyone to search the entire internet for webcams.
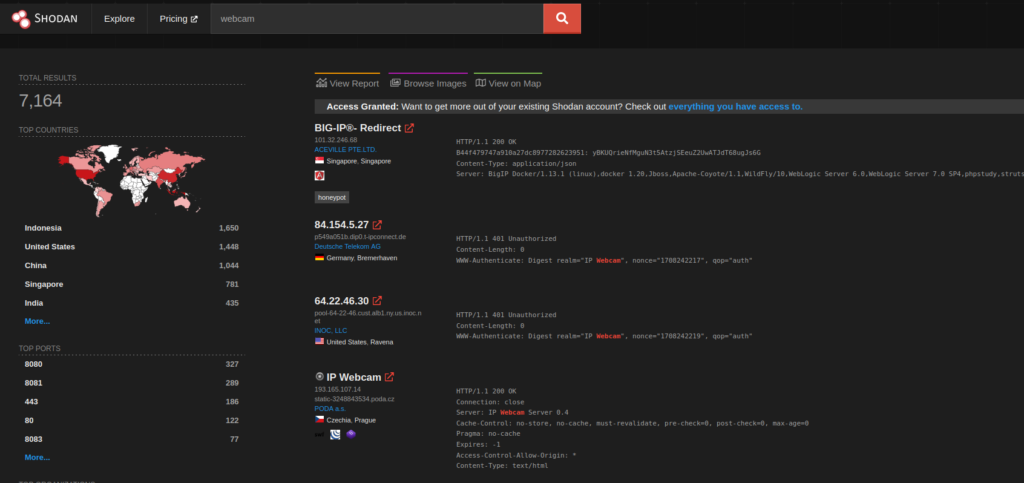
Shodan IoT Security search engine
This is a quick search I performed for this article. I did not log in with an account, so the amount of returned data is less than if I had used a free account. However, even with a free account, we can see 7,164 available webcams. This doesn’t mean that all of these do not require a password to access, but it means they are live on the web and not being filtered. From here, an attacker could run an automated credential attack using something like Hydra until it had broken in.
With tools like Shodan, attackers don’t need a lot of skill to exploit improperly secured IoT devices.
If that wasn’t enough to concern you, there are entire channels on YouTube created to showcase a trend where an attacker will find a nanny cam or home security camera that is unsecured. They will then take over the device and use it to watch the family that owns it. Several years ago, it became a sport to see how far they could go, using the device’s microphones to talk to the families. They would also post videos of what they had been able to see. Imagine your own home and what your cameras may have seen, and it will give you an idea of what types of videos these attackers captured.
Take steps to secure yourself or your practice
Taking some precautions can provide some IoT security and help keep your network and data secure. Even when a vendor fails to implement even the most basic of security guidelines, these can help reduce your overall risk of exposure.
Ensure all devices are behind a firewall
For cybersecurity professionals, this seems like a no-brainer. However, it is shocking how many IoT devices are installed on networks without any form of firewall protection. All IoT devices should be placed behind a perimeter firewall appliance and not directly connected to the Internet.
Install all devices on their own segregated network
All IoT devices should be segregated to their own VLAN or network segment. From there, access to and from this segregated network should be filtered to only what is necessary. For example, if you have a network video recorder (NVR) and cameras, they should be on their own network. All administration or viewing of the footage should be performed from an administrator computer. Ideally, it would be the only device on the private network that could access the NVR and NVR would not be able to access the private network at all. Unfortunately, this isn’t always possible, but in nearly all cases, some form of segregation can be used to provide better security.
Limit the number and types of devices used
Before purchasing and adding an IoT device to your network, make sure you really need it. Is it absolutely necessary? Can it be properly secured once it has been added? Are there alternatives that don’t involve the IoT? Each device increases the surface area for attacks. By limiting the number installed, you can help keep minimizing this area.
Change default credentials on IoT devices
This is one of the most important. Don’t leave rhe default admin password. Change it to something far more secure. You can read our guide to creating secure passwords here. If your device will let you rename the admin account, or create a new account and then disable the admin account, do that. This makes gaining access a lot harder. If the username is admin, then the attacker already has half of the information they need to get in.
Install vendor-supplied updates and patches to devices
Keep your devices up-to-date with all patches or updates released by the vendor. This is extremely important as these updates often address security vulberabilities that have been found. Be sure to check at least monthly. If you are responsible for a large number of IoT devices, this can be extremely time consuming but it is still necessary.
Monitor IoT devices for signs of attacks
Most devices have SNMP capabilities. Others are Linux devices that allow you to install additional apps, such as Zabbix, onto them. However, this isn’t common. Locate the manner that your devces allow for monitoring and set up a way to capture thiis data. From there, you can use this to help catch when one is under attack. Attempting IoT security with monitoring is a recipe for disaster.
Perform regular audits
Periodically, assess whether you still need all the devices you have connected. Can you remove any of these devices? Do any need to be replaced or upgraded? What can you do to improve the overall IoT security posture be improved? It’s easy to install a device and then forget about. We need to go back through, from time to time, to make sure we still actually need them.
The IoT has brought about a new level of data access and also conveience. However, with all new technology comes a whole new class of vulnerabilities. Following the steps outlined above will help ensure that you are able to make use of these devices in a secure manner and not endnager your personal data or that of your patients.
