One of the biggest external threats to a practice’s Protected Health Information (PHI) is phishing. This can be seen in many breaches that are reported to the Department Of Health and Human Services. A recent example shows why this is such a serious threat to small practices.
Catawba Valley Medical Center in North Carolina was breached on three separate occasions due to phishing email sent to employees. The attack exposed the records of 20,000 patients.
What happened?
On August 12, officials discovered that an employee email account had been breached in what appeared to be a phishing attack. They immediately contacted an outside computer forensics team who determined ii was actually two accounts that had been breached. One the accounts had been attacked twice. The period of time last for several weeks. Patient names, dates of birth, medical data, insurance payment information, and some Social Security numbers we impacted as a result of the successful attack.
Catawba Valley Medical Center setup a call center for patients to call in for information. They began contacting patients on October 12th to advise them of the breach, as is required under law. Afterwards, Catawba Valley hired outside computer security experts to help train their staff and also improve the security of their email system.
What is phishing?
Phishing is when an attacker sends an email to a potential victim with a link in the email. The victim will click on the link and be taken to a site where they will be asked to fill in their information such as usernames and passwords. The email will be made to look like it is coming from a legitimate source that will entice the victim into complying. The site that the victim visits will not be a real site, but one made to look as close to a legitimate site as possible. Once the victim enters their information in, the attacker has all the details.
In another form of phishing, the attacker may send an attachment that appears to be legitimate. It may be an invoice for a service or something from a bank or credit card company. Once the victim opens the attachment, malware hidden inside is ran and the victim’s machine will become infected. This will usually be some form of remote access tool that will give the attacker access to the victim’s computer. In the case of HIPAA attacks, this is the most likely form. Once the attacker has access to the victim’s computer, they can install key loggers to capture the user’s user names and passwords. This would then give them access the practice’s EMR and billing systems.
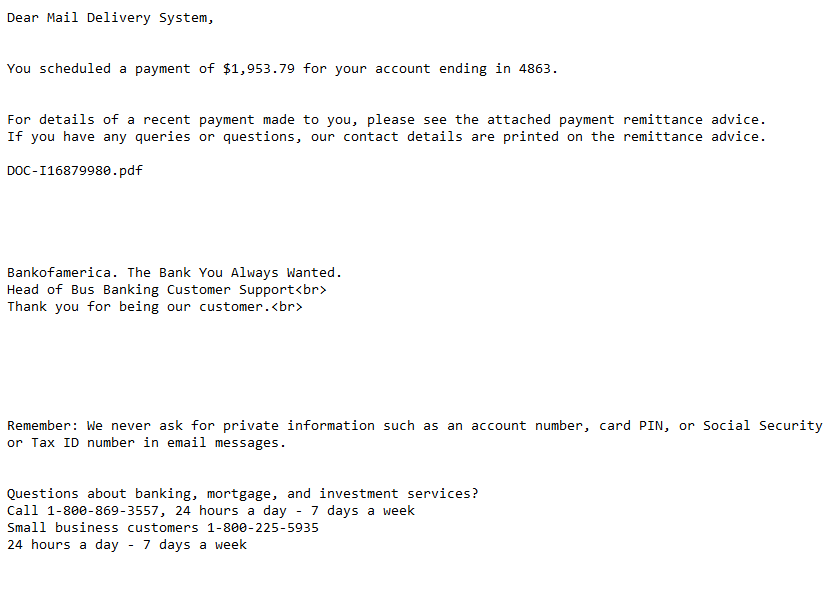
Above is a real example of a phishing email I received recently. It had an attachment on that when I studied it, contained malware. Notice the spelling of Bank of America (Bankofamerica). Head of Bus Banking Customer Support? Is that supporting customers while they ride on a bus? You will notice spelling and grammar mistakes in this email. But what they are betting on is that you will see that a large amount of money is being transferred and you will freak out. You might open the attachment and to see what is going on and then it will be too late.
Why is this so serious?
Most practices don’t have much budgeted for computer security. They focus their funds on EMRs, computers, servers, and medical equipment. But having security devices such as firewalls installed isn’t enough. Someone has to be monitoring the logs that these devices generate. Its like having an alarm system that when triggered, doesn’t call the police department. This type of attack could be found if someone was watching the network for large amounts of data leaving the network. But that takes training or someone to actually monitor for attacks. Breaches like this can go on for weeks or months without anyone ever knowing.
How to protect your practice from phishing
The first step is to train your staff what phishing attacks look like. Train them to be suspicious of anyone asking for information online. For example, if you get an email from your bank saying that money has been transferred from your account, don’t click on any links that may be in the email. Open a browser and type in the address of your bank and login manually.
Make sure you have quality malware protection software installed on your computers. Free versions of these programs aren’t going to protect you. The free versions don’t include real time protection that watches your computer as you go about your day. This will protect you when you try to open attachments in email.
Don’t open attachments from people you don’t know. When you do know them, make sure it is something you are expecting and not a random email with a attachment on it.
Make sure you the proper controls in place for your practice. Do you have a firewall? Is it monitored? Do you require strong passwords for all user accounts? Is account access on all computers being logged and monitored?
Following these steps will greatly minimize your risk to being compromised with a phishing attack.
[DISPLAY_ULTIMATE_SOCIAL_ICONS]
