Phishing attacks may be the most threatening to healthcare entities as well as companies in the United States. According to some estimates, phishing attacks increased 59% in 2017 alone. Most attackers know this is the easiest way to breach a target. It requires little effort and once its up and running, the attacker just sits back and waits for the victims to arrive. Phishing attacks are very common and extremely effective.
For HIPAA Covered Entities and Business Associates, these can not only be expensive (an estimated $1.6 million on average), but can result in breaches. These breaches can turn into expensive fines and corrective action plans. This can be seen in the case of Cancer Treatment Centers of America. A phishing attack resulted in a breach of 41,948 patient’s data.
What happened
In September 2018, the practice discovered that an email account belong to an employee of the practice had been hacked. The account was hacked in May of 2018. A single employee had received an email that appeared to originate from an executive of Cancer Treatment Centers of America. The employee shared login credentials via the email and this resulted in a network breach. The user was later directed to change their password by IT services.
The result
Potentially, 41,948 patient records were breached as a result of the phishing attack. An investigation was completed internally and an HHS investigation will determine what, if any, fines or corrective action plans will be required.
What is a phishing attack?
A phishing attack is when an attacker sends an email to an organization (or individual), pretending to be something else in an effort to get the user to provide information or click on links. These links will often result in malware being installed on the user’s computer that will give the attacker remote access to the network.
These emails use social engineering to nudge the victim into making the choice the attacker needs. For example, an email may appear to be from UPS indicating your package from Amazon has been delayed and to click the supplied link to get an update in the new delivery time. At any given moment, many people are receiving a package from Amazon so this creates the curiosity to click on the supplied link.
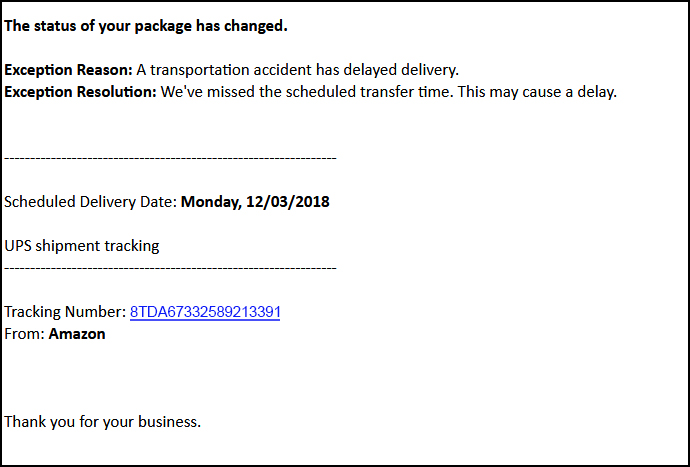
The link appears to be the tracking number so that the victim can quickly check the status of the delivery. This link leads to a page that will deploy malware onto the victim’s computer. In some cases, the email may contain an attachment that when opened, does the same thing.
In this case, the email appeared to come from an executive within the practice. This preys on the victim’s fear of not complying with the directives of a superior. This is a common attack method. Emails appearing to come from the IRS or other government agencies will demand the victim comply with an action.
Another favorite technique is to send an email appearing to come from a business owner to another employee with a subject of ’employee termination list’. The email will appear to be miss-sent to the wrong employee. If an employee received an email like this, thinking it was meant for a manager or another employee, but they received it instead, they may open the attachment to see the list of employees that were supposed to be terminated.
The attacker is preying on your fear or curiosity.
Summary
Phishing attacks are the easiest way for an attacker to breach an organization. They don’t require a lot of work and have the chance of a big payoff. In the case of Cancer Treatment Centers of America, a single email account resulted in a breach of 41,948 patient records. Office staff needs to have training on how to spot phishing attacks and also the practice needs to put the necessary preventative measures in place to ensure these attacks don’t result in HIPAA breaches.
[DISPLAY_ULTIMATE_SOCIAL_ICONS]